Palo Alto Firewall Search Syntax
Decide which search strings to filter. Frommember eq trust and tomember eq dmz and destinationmember eq webserver hope this helps.
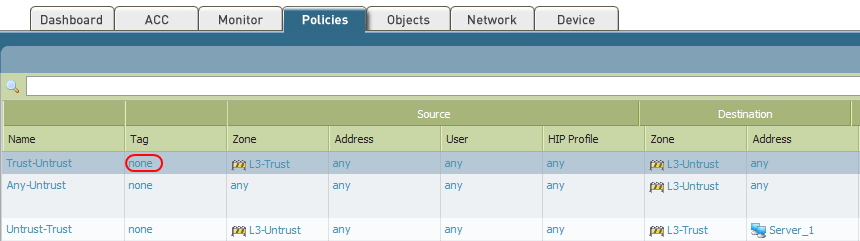 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
Create test new rule playbook hosts.
Palo alto firewall search syntax. A user can access first-time configurations of Palo Alto Networks next-generation firewalls via CLI by connecting to the Ethernet management interface which is preconfigured with the IP address 19216811 and have SSH services enabled both by default. To see and sort the applications seen on a rule in the rules row click. Accessing the CLI of your Palo Alto Networks next-generation firewall.
View policy rule usage to simplify your rule lifecycle management to find and delete unused rules to maintain an up-to-date rulebase and improve your Security posture. When Trying to search for a log with a source IP destination IP or any other flags Filters can be used. Add test pre-rule to panorama.
As you can see there is a filter which will automatically create a filter string. For example filtering by the rule UUID makes it easier to pinpoint the specific rule you want to locate even among many similarly-named rules. Quit with q or get some h help.
The CLI is a no-frills interface that. Proxy bypassfilter myspace facebook proxy bypassfilter myspace facebook. The following example will search on the range of IP addresses from 1010100 - 101010255.
332020 So i am very new to using ansible with PanoramaPalo Alto firewall. The hard way is to actually type full search strings in the search field. Palo Alto Networks Inc.
The filters need to be put in the search section under GUI. This graphical interface allows you to access the firewall using HTTPS recommended or HTTP and it is the best way to perform administrative tasks. To learn more about the security rules that trigger the creation of entries for the other types of logs see Log Types and Severity Levels.
Source or Destination address addrsrc in xxxx or addrdst in xxxx Traffic for a specific security policy rule. The following example will filter on URL logs that contain the word google. However it is also the most complicated search syntax and is completely different than traditional SPL search language so it takes some getting used to.
Wildcards cannot be used in the filter but summarizing and specifying the subnet in the filter can be done. If the UUID of a rule changes the application usage statistics for that rule reset because the UUID change makes the firewall see the rule as a different new rule. If your ruleset is very large and contains many rules using the rules UUID as a filter spotlights the particular rule you need to.
While youre in this live mode you can toggle the view via s for session of a for application. At the core of this platform is the next-generation firewall which delivers visibility and control over applications. The easy way is to use the dropdown menu for any of the collumns.
Search for multiple source addresses using the or. Additional ResourcePalo Alto Log Types. Create a text file using Notepad.
Lastly we can use traditional searches. 3192021 You can view the different log types on the firewall in a tabular format. Use the Command Line Interface CLI to perform a series of tasks by entering commands in rapid succession over SSH recommended Telnet or the console port.
Over-provisioned access on the firewall can be exploited by attacks so administrators need to periodically check for outdated and unused rules. Traffic or other logs. These are two handy commands to get some live stats about the current session or application usage on a Palo Alto.
Here is my yml file ---- name. 432019 To build out your own query move to the next section Log Filter Syntax Reference. Additionally the next-generation firewalls have a console.
This document demonstrates several methods of filtering and looking for specific types of traffic on Palo Alto Networks firewalls. The firewall locally stores all log files and automatically generates Configuration and System logs by default. 6262017 you can use a more complex search string to search for a specific type of policy and if you want you can create these in advance so youd only need to copypaste them into the search bar eg.
See the following examples below. Install the Palo Alto Networks App for Splunk. 3192021 Filter logs by artifacts that are associated with individual log entries.
Log Filter Syntax Reference. It contains a full datamodel for all Palo Alto Networks logs which. I am doing a test on my test lab pano to see if i can push test rule over to panorama.
PAN-OS 50 60 example. This technique does not pull from the index so there are a couple things you need to configure before using it. In PAN-OS 90 Rule Usage Filtering enables you to quickly filter.
Has pioneered the next generation of network security with an innovative platform that allows you to secure your network and safely enable an increasingly complex and rapidly growing number of applications. Otherwise the URL cannot be determined by the Palo Alto Networks firewall.
 Palo Alto Networks Firewall Concepts Cyber Security Service
Palo Alto Networks Firewall Concepts Cyber Security Service
How To Create A New Service Object Knowledge Base Palo Alto Networks
How To Manually Import And Install Pan Os From The Cli Knowledge Base Palo Alto Networks
 Palo Alto Networks Firewall Concepts Cyber Security Service
Palo Alto Networks Firewall Concepts Cyber Security Service
How To Display The Log Filter Expressions Knowledge Base Palo Alto Networks
How To Configure Color Coded Tags Knowledge Base Palo Alto Networks
Basics Of Traffic Monitor Filtering Knowledge Base Palo Alto Networks
 How To Install And Configure Palo Alto In Gns3
How To Install And Configure Palo Alto In Gns3
 Configuring Palo Alto Networks Wildfire And Tanium Threat Response
Configuring Palo Alto Networks Wildfire And Tanium Threat Response
How To Identify Unused Policies On A Palo Alto Networks Device Knowledge Base Palo Alto Networks
 Palo Alto Networks 1 Initial Configuration For Beginners Rtodto Net
Palo Alto Networks 1 Initial Configuration For Beginners Rtodto Net
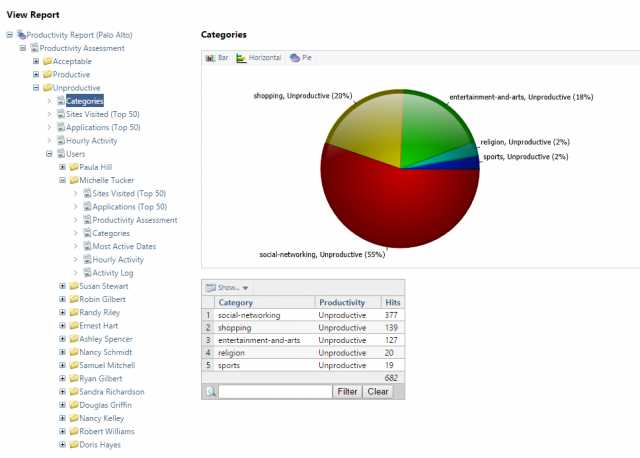 Web Activity Reporting With Palo Alto Firewall Log Files
Web Activity Reporting With Palo Alto Firewall Log Files
Getting Started Packet Capture Knowledge Base Palo Alto Networks
How To View The Hostname In The Monitor Logs Knowledge Base Palo Alto Networks
How To Filter Bgp Routes Imported Into The Firewall Routing Tab Knowledge Base Palo Alto Networks
How To Perform Policy Match And Connectivity Tests From The Web Knowledge Base Palo Alto Networks
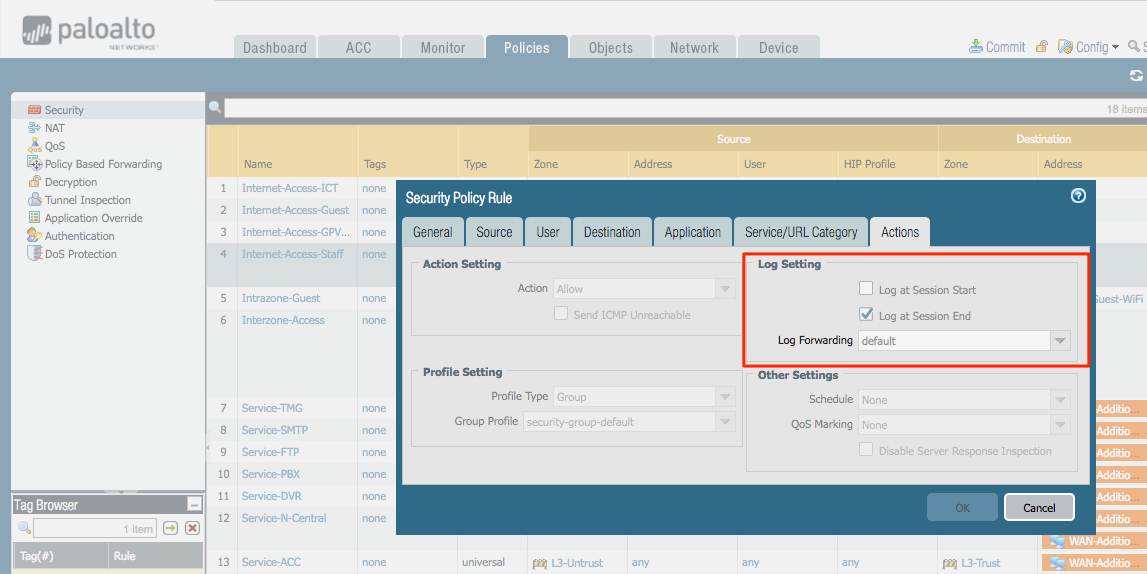 How To Configure Palo Alto Networks Logging And Reporting
How To Configure Palo Alto Networks Logging And Reporting
How To Add Exempt Ip Addresses From The Threat Monitor Logs Knowledge Base Palo Alto Networks

Posting Komentar untuk "Palo Alto Firewall Search Syntax"