Palo Alto Networks Firewall Zero Trust
Remember the point of infiltration of an attack is often not the target location. Its time for a paradigm shift in cybersecurity.
 Palo Alto Networks Portfolio Strategy Overview 2019
Palo Alto Networks Portfolio Strategy Overview 2019
The report states Palo Alto Networks has a complete toolkit for Zero Trust to deliver Zero Trust everywhere on-premises in the data center and in cloud environments.

Palo alto networks firewall zero trust. One of the major areas of concern for ICS and SCADA operators is unsegmented networks and cybersecurity professionals agree that network segmentation is a crucial step in network security. At the heart of the worlds first ML-Powered Next-Generation Firewall is the new PAN-OS 100 - empowering you to stay ahead of unknown threats see everything including IoT and reduce errors with automatic policy recommendations. Traffic the asserted identity generates must be inspected for malicious content and unauthorized activity and logged through Layer 7.
Panroma centralizes management policy control for multiple next-generation firewalls and increases operational efficiency compared to managing firewalls. The Palo Alto Networks next-generation firewall brings a unique combination of hardware and software functionality that makes it ideal as a Zero Trust network segmentation gateway. 3192021 Over the last few months ESG surveyed 421 IT and cybersecurity professionals at organizations in North America US and Canada personally responsible for driving zero-trust security strategies and evaluating purchasing and managing security technology products and services in support of Zero-trust initiatives.
Zero Trust policy consists of whitelist rulesrules that allow only authorized users to access specific resources using the specified applications at the right time in the right places. The Zero Trust model recognizes that trust is a vulnerability. Read Secure the Cloud Secure the Enterprise Secure the Future Zero Trust Security.
Thales SafeNet Trusted Access STA enforces a broad range of authentication methods at the access point while the Palo Alto Networks NGFW inspects traffic enforces network security policies and delivers threat prevention enabling organizations to achieve Zero Trust network. Once on the network users including threat actors and malicious insiders are free to move laterally and access or exfiltrate whatever data they are not limited to. 1192021 A Zero Trust approach of never trust always verify is most effective when it spans all the locations and environments where workloads power and run your applications and data.
A key component of Palo Alto Networks Next-Generation Security Platform is Traps advanced endpoint protection which employs multiple methods of protection at critical stages of the attack lifecycle to prevent known and unknown malware exploits and ransomware as well as zero. Introduction Zero Trust Zero Trust Environment Zero Trust Architecture Zero Trust Design Principles Data Assets Applications. This is in stark contrast to the traditional perimeter security model which presumes that bad actors are always on the untrusted side of the network and trustworthy users are always on the trusted side.
Welcome to the era of intelligent network security. Identity is only part of Zero Trust. Palo Alto Networks enables you to architect your Zero Trust environment and apply consistent security across all locations.
By applying the Zero Trust mantra Never trust always verify organizations can ensure proper user context through authentication and attribute verification before allowing access to apps and data in the cloud or data center. Palo Alto Networks Is a Forrester ZTX Wave Leader By Nir Zuk September 24 2020 at 1015 AM 2 min. Watch our on-demand webinar designed specifically for ICS and SCADA professionals and youll.
Thats why our firewall platform significantly bolsters a Zero Trust architecture by moving network security as close to workloads as possible and there are six primary. The integration of key security functions in the network segmentation. Next-Generation Security Platform is designed to enable and align to a Zero Trust architecture.
A true ZTNA approach requires full content inspection to identify users and ensure. A Zero Trust approach is the answer. Zero Trust eXtended Ecosystem Platform Providers Q3 2020.
Services DAAS Protect Surface Segmentation Gateway Microperimeter Microsegmentation Asserted Identity Least-privilege Access Granular Access Control Trust Levels Data Toxicity The 5 Steps to Implementing. 162020 Therein lies the need for Zero Trust Network Access ZTNA. Zero Trust Throughout Your Infrastructure Archives - Palo Alto Networks Blog.
This is important because. The cloud-delivered security service can be enabled on any of our Next Generation Firewalls for current customers or delivered as a complete solution for non-Palo Alto Networks. Zero Trust is an IT security model that eliminates the notion of trust to protect networks applications and data.
Start with the protect surface the sensitive data you want to protect and extend across the network to the applications systems and. 922020 Implementing Zero Trust for IoT Environments With Palo Alto Networks IoT Security. Zero Trust Network Access ZTNA Enable Zero Trust Network Access for your employees anywhere in the world with encrypted application access authentication policy management and threat detection in a single solution.
Zero Trust is all about identity. Palo Alto Networks IoT Security brings IoT devices into the fold of a Zero Trust security model by implementing four best practices that minimize IoT security risks and keep your network safe from cyber attacks. If traffic doesnt match a rule the firewall automatically blocks the traffic.
Palo Alto Networks was named a Leader in The Forrester Wave.
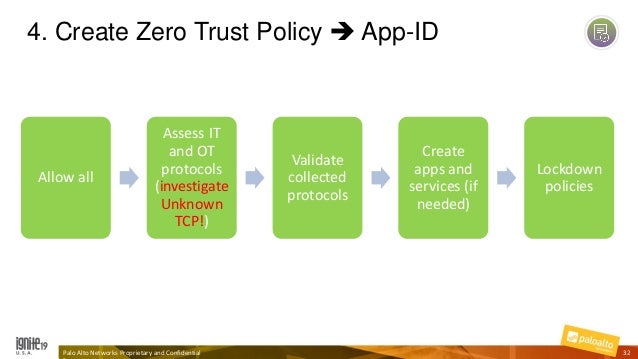
 Simplify Zero Trust Implementation With A Five Step Methodology Rantek
Simplify Zero Trust Implementation With A Five Step Methodology Rantek
 Zero Trust A Transformation Roadmap
Zero Trust A Transformation Roadmap
 New Integration From Cryptonitenxt And Palo Alto Networks Provides Best In Class Security To Secure Iot And Shut Down Advanced Threats Cryptonitenxt
New Integration From Cryptonitenxt And Palo Alto Networks Provides Best In Class Security To Secure Iot And Shut Down Advanced Threats Cryptonitenxt
 Simplerna Gallery Of Enterprise Ads Juniper To Palo Alto Networks Palo Alto Networks Juniper Networks Networking
Simplerna Gallery Of Enterprise Ads Juniper To Palo Alto Networks Palo Alto Networks Juniper Networks Networking
 How To Architect Zero Trust Network Segmentation In Industrial Control Systems Palo Alto Networks
How To Architect Zero Trust Network Segmentation In Industrial Control Systems Palo Alto Networks
 Zero Trust Network Architecture With John Kindervag Network Architecture Cyber Security Networking
Zero Trust Network Architecture With John Kindervag Network Architecture Cyber Security Networking
 Merry Christmas Happy New Year Merry Christmas And Happy New Year Palo Alto Networks Happy New
Merry Christmas Happy New Year Merry Christmas And Happy New Year Palo Alto Networks Happy New
 Business Case For Next Generation Firewalls Business Case Palo Alto Networks Generation
Business Case For Next Generation Firewalls Business Case Palo Alto Networks Generation
 Pan Os Security Operating Platform Single Pass Architecture Zero Trust Secu Palo Alto Networks Youtube
Pan Os Security Operating Platform Single Pass Architecture Zero Trust Secu Palo Alto Networks Youtube
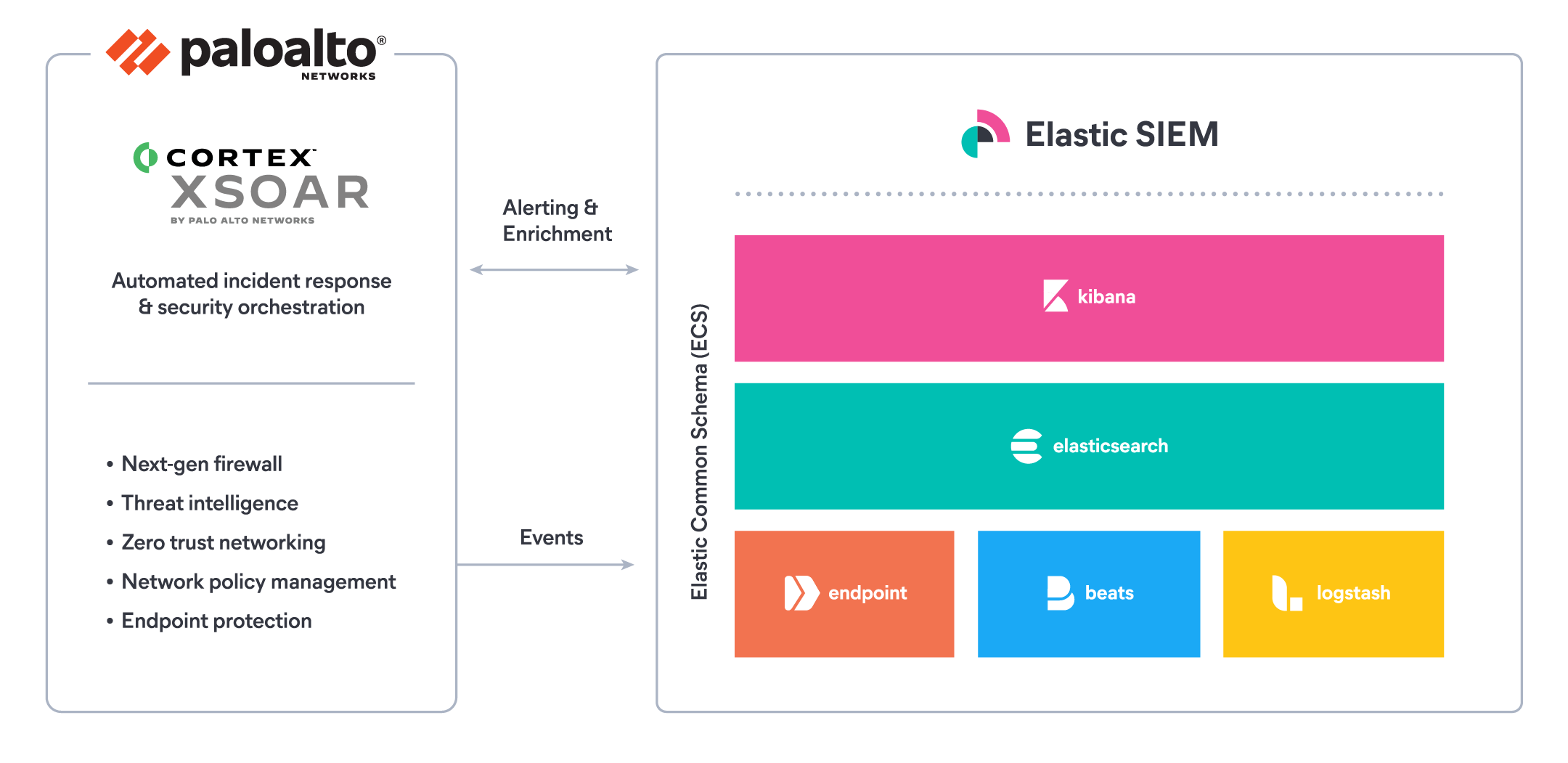 Palo Alto Networks Elastic Stack Integration Elastic Partners
Palo Alto Networks Elastic Stack Integration Elastic Partners
 11 Zero Trust Networking Palo Alto Networks Zero Trust Networking April 2015 C 2014 Palo Alto Networks Confidential And Proprietary 1 Greg Kreiling Ppt Download
11 Zero Trust Networking Palo Alto Networks Zero Trust Networking April 2015 C 2014 Palo Alto Networks Confidential And Proprietary 1 Greg Kreiling Ppt Download
 Zero Trust Throughout Your Infrastructure With Nir Zuk Founder And Cto Of Palo Alto Networks Youtube
Zero Trust Throughout Your Infrastructure With Nir Zuk Founder And Cto Of Palo Alto Networks Youtube
 Stephan Burgerman Sburgerman Twitter
Stephan Burgerman Sburgerman Twitter




Posting Komentar untuk "Palo Alto Networks Firewall Zero Trust"