Palo Alto Firewall Rule Example
That allows all traffic from Trust zone to Untrust zone. Ansible test rule 0.
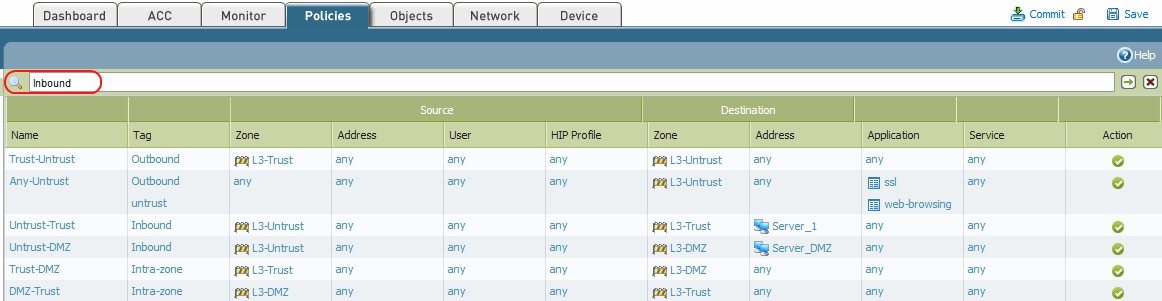 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
Task Example.
Palo alto firewall rule example. - name. Will be 1111 and connected to Ethernet 11. State is defined --- Derive firewall.
Any rule that is not using App ID in the Application column of the rule should be converted to App ID. When the traffic hits the Firewall the destination IP is translated to the private IP of 1721611o. Placing the letter n in front of eq means not equal to so anything not equal to deny is displayed which is any allowed traffic.
To copy files from or to the Palo Alto firewall scp or tftp can be used. The underlying protocol uses API calls that are wrapped within the Ansible framework. I just happen to have access to one of these devices and wished to get some logs into OSSEC.
From panosfirewall import Firewall fw Firewall10001 admin mypassword version fwrefresh_system_infoversion print version. Please remember that you also need corresponding Security Rule to allow http traffic from the Internet to the web-server. 11112019 Manage security rules on a Palo Alto Firewall Requires.
Note that these rules also permit traffic from an internal zone to the interface of the Palo Alto firewall itself eg for ping oder DNS Proxy. Public IP address to be used from ISP A. Shows all traffic allowed by the firewall rules.
2102013 I found a great Palo Alto document that goes into the details and Ive broken down some of the concepts here. Panos_object_serviceyaml Vars Example. The easiest way to find that out is to enable debugging in the CLI and then execute the command that would achieve the result you are looking for.
A single bidirectional rule is needed for every internal zone on the branch firewall. For example when you migrate port-based rules to app-based rules you create an app-based rule above the port-based rule and check for any traffic that matches the port-based rule. When a Palo Alto Networks firewall has access to two or more service providers creating an inbound NAT rule has to be done differently because of the fact that inbound traffic might come from either ISP.
For example you can create a custom URL Category to specify a group of sites you need to access for business purposes but that dont support the safest protocols and algorithms and then apply a customized Decryption profile to allow the looser protocols and algorithms for just those sites that way you dont decrease security by downgrading the Decryption profile you use for most sites. 3232013 OSSEC Palo-Alto. A little search on the interwebs only turned up a single relevant link.
Grab the credentials from ansible-vault include_vars. You can either delete the rule or modify the rule to reflect your zone naming conventions. OSSEC currently does not include any decoders or rules for Palo-Alto Networks Next-Generation firewalls.
App ID is one of the crown jewels of the Palo Alto Networks next generation firewall technologies the ability to identify what application is being used on any given flow through the firewall. Then move on to the translation packet tab and set the destination as with the regular rule to 192168097. For example if you have a packet that arrives at the firewall with.
Palo Alto will then show you the syntax it passed and you can use that as a model. 192168110 your private Destination IP. You can see complete examples here.
In order to limit the management access of the Palo Alto interfaces Interface Mgmt profiles can be used. The commands have both the same structure with export to or import from eg. Interface ethernet12 Internal Interface of the Firewall IP Address 192168023024 If we add a new rule name it internal access go to the original packet tab and set the source zone to trust destination zone to untrust and set the destination address to 19851100230.
Create panos security rule. After migration the hit-count data helps you determine whether the port-based rule is safe to remove by confirming whether traffic is matching the app-based rule instead of the port-based rule. A collection of Ansible modules that automate configuration and operational tasks on Palo Alto Networks Next Generation Firewalls both physical and virtualized form factor.
132021 In this example we have a web-server which is reachable from the Internet via Firewalls OUSIDE IP of 200101010. Get the version of a firewall. View on GitHub Examples.
Wait for SSH timeout 10min wait_for. Turn on debugging debug cli on. For example to get the syntax for adding a security rule.
3192021 By default the firewall includes a security rule named. 3192021 On a Palo Alto Networks firewall individual Security policy rules determine whether to block or allow a session based on traffic attributes such as the source and destination security zone the source and destination IP address the application the user and the service. Port22 host providerip_address search_regexSSH.
All Traffic Denied By The FireWall Rules. NAT policies are always applied to the original unmodified packet. Xavier Mertens wrote a quick blog post during the second.
We use refresh_system_info here instead of an op commands because this method saves the version information to the Firewall object which tells all.
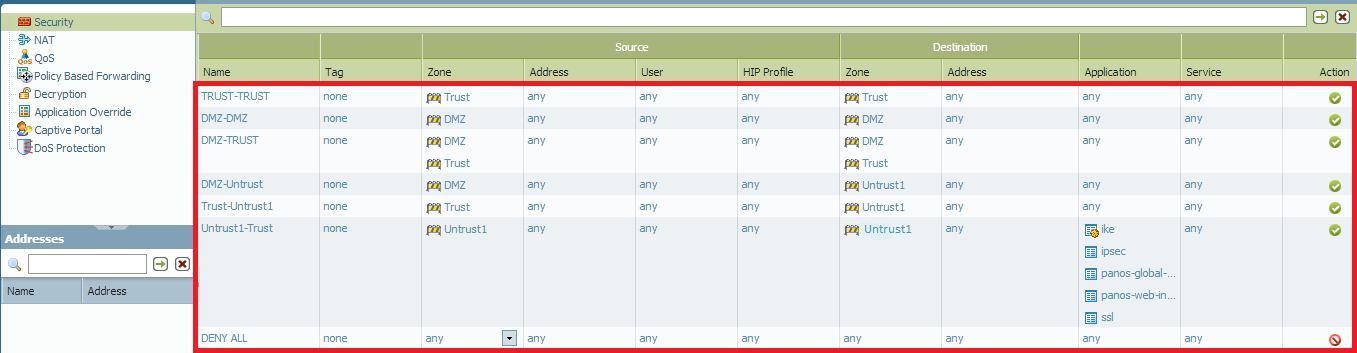 Any Any Deny Security Rule Changes Default Behavior Knowledge Base Palo Alto Networks
Any Any Deny Security Rule Changes Default Behavior Knowledge Base Palo Alto Networks
How To Configure A Palo Alto Networks Device For Tap Mode Opera Knowledge Base Palo Alto Networks
Security Policy Fundamentals Knowledge Base Palo Alto Networks
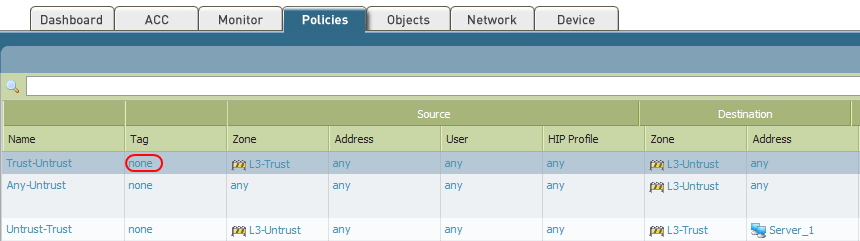 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
 Palo Alto Firewall Initial Config Youtube
Palo Alto Firewall Initial Config Youtube
Security Policy Fundamentals Knowledge Base Palo Alto Networks
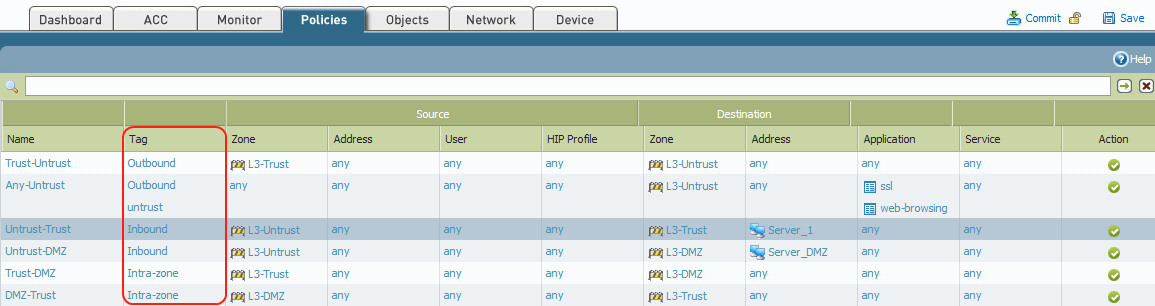 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
Basics Of Traffic Monitor Filtering Knowledge Base Palo Alto Networks
Evaluation Order Of Panorama Pushed Security Policies Knowledge Base Palo Alto Networks
How To Identify Unused Policies On A Palo Alto Networks Device Knowledge Base Palo Alto Networks
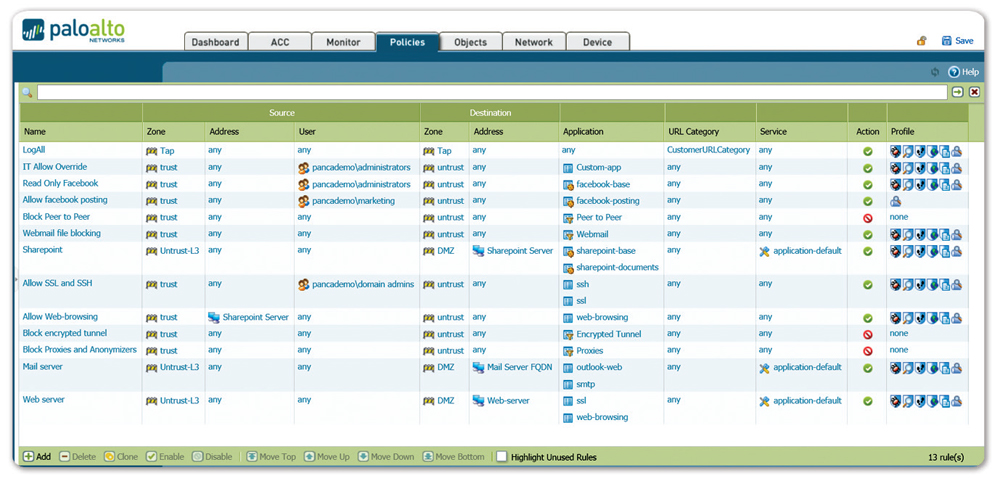 Palo Alto Networks Vm 100 מוצרי פאלו אלטו
Palo Alto Networks Vm 100 מוצרי פאלו אלטו
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
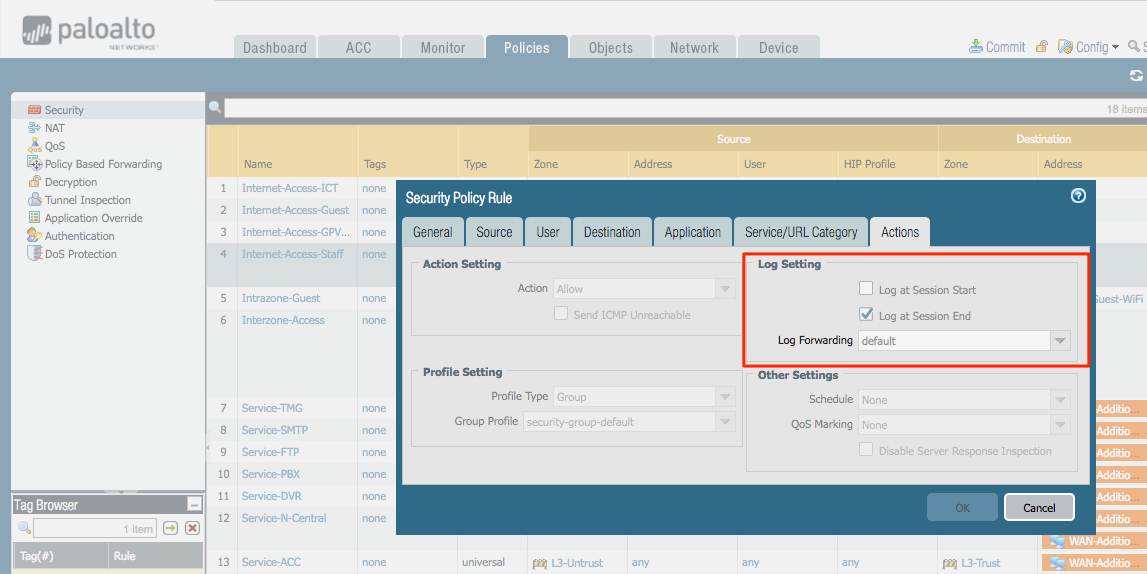 How To Configure Palo Alto Networks Logging And Reporting
How To Configure Palo Alto Networks Logging And Reporting
Security Policy Fundamentals Knowledge Base Palo Alto Networks
 Palo Alto Networks Agentless User Id Tutorial Youtube
Palo Alto Networks Agentless User Id Tutorial Youtube
How To Configure Color Coded Tags Knowledge Base Palo Alto Networks
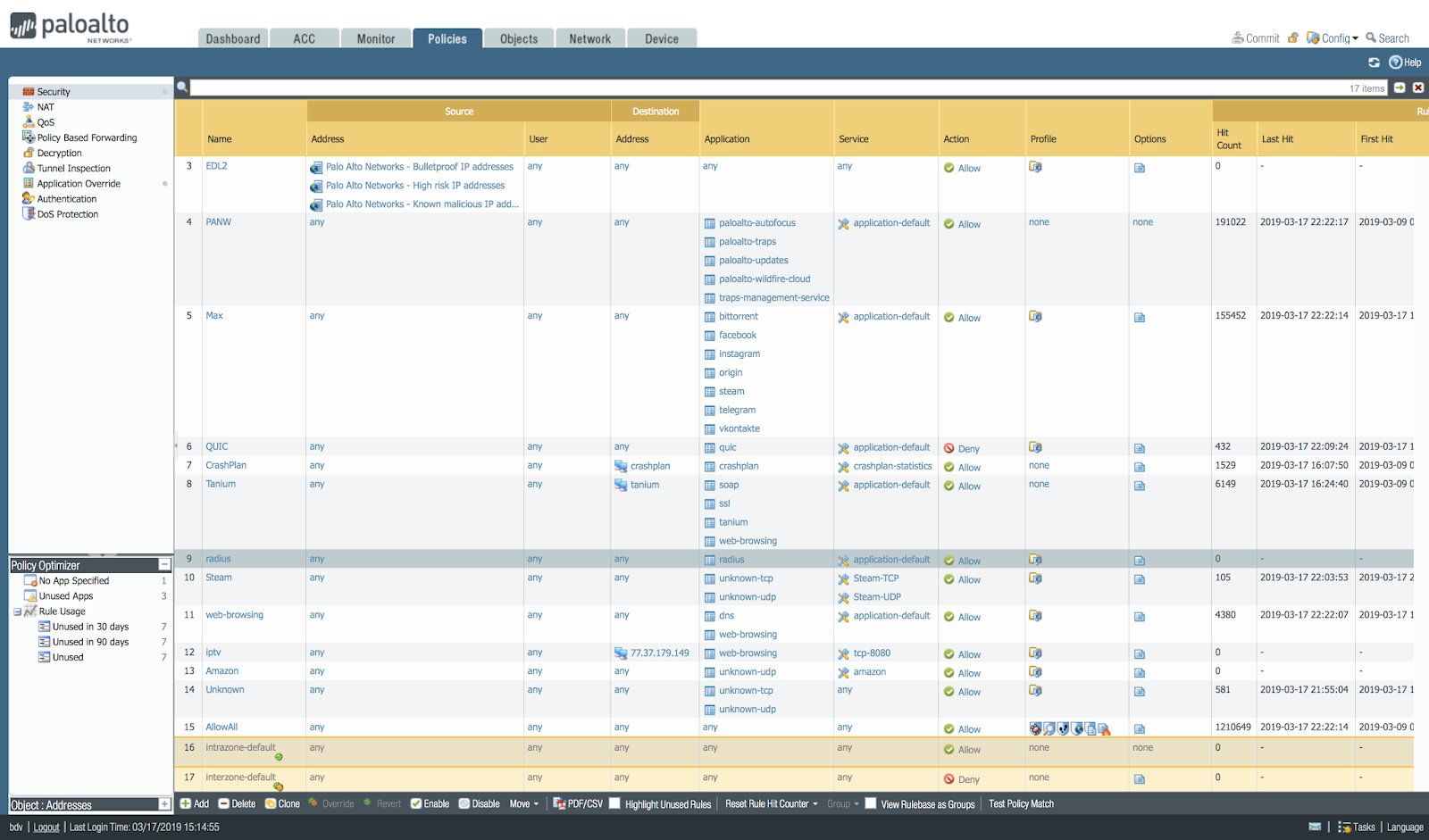 Palo Alto Networks Ngfw Security Policy Optimizer Sudo Null It News
Palo Alto Networks Ngfw Security Policy Optimizer Sudo Null It News
 Palo Alto Networks Firewall Configuration For Vidyo Vidyocloud Support
Palo Alto Networks Firewall Configuration For Vidyo Vidyocloud Support
Posting Komentar untuk "Palo Alto Firewall Rule Example"