Palo Alto Firewall Rules Best Practice
We put our five years of experience in designing implementing supporting and managing Palo Alto Networks solutions together and wrote this guide to share our best practices to secure an enterprise network using a Palo Alto Networks Next-Generation FireWalls. Use the predefined strict file blocking profile to block files that are commonly included in malware attack campaigns and that have no real use case for uploaddownload.
Best Practices for Deploying Content Updates.

Palo alto firewall rules best practice. After you Identify Your Application Allow List you are ready to create the next part of the best practice internet gateway security policy rulebase. Whether youre looking for the best way to secure administrative access to your next-gen firewalls and Panorama create best practice security policy to safely enable application access at the internet gateway and the data center or learn the best way roll out a decryption policy to prevent threats from sneaking into your network you will find the guidance you need here in our best practice documentation. Each check is a best practice identified by Palo Alto Networks security experts.
Use these File Blocking settings as a best practice at your internet gateway. Targeting decryption and phasing it in based on URL categories are also Decryption best practices. Access to the Management interface or possibly any other data interface designated for administration should be always restricted and never enabled for connections originating in untrusted zones such as the Internet.
A firewall is only as good as the features that you take advantage of. On Tuesday 27th of October 2020 we run this training workshop for Palo Alto Networks. Share Threat Intelligence with Palo Alto Networks Permit the firewall to periodically.
It gives a taste of the new course by teaching a full module. Exclude certain web traffic from decryption Use URL categories to make decryption exceptions especially if you want to exclude certain types of sites from decryption because of privacy concerns for example financial-services and health-and-medicine sites. This page will provide more information about this feature.
The application allow rules. It gives a taste of the new course by teaching a full module. Every allow rule you create must allow traffic based on application not port and with the exception of certain infrastructure applications that require user access before the firewall can identify the user.
On Tuesday 27th of October 2020 we run this training workshop for Palo Alto Networks. Follow the Best Practices for Securing Your Network from Layer 4 and Layer 7 Evasions. 3192021 Use decryption on a firewall to prevent malicious content from entering your network or sensitive content from leaving your network concealed as encrypted or tunneled traffic.
Palo Alto Next-Generation Firewalls natively support OOB through a dedicated Management interface. Strengthen your security with a best practice implementation. The BPA component performs more than 200 security checks on a firewall or Panorama configuration and provides a passfail score for each check.
3122020 Introducing the all-new Improving Security Posture and Hardening PAN-OS Firewalls. And our best practice. Firewall Hardening Best Practices for Palo Alto Networks.
The Palo Alto Networks Best Practice Assessment BPA measures your usage of our Next-Generation Firewall and Panorama security management capabilities across your deployment enabling you to make adjustments that maximize your return on investment and strengthen security. If you own Palo Alto Networks Next-Generation Firewalls and manage software updates including Dynamic Updates learn best practices and recommendations to ensure smooth deployment of weekly content from Palo Alto Networks. 4222020 Best Practice Assessment 99 of firewall breaches through 2023 will be due to firewall misconfigurations not firewall flaws according to Gartner research1 Companies typically implement basic capabilities and postpone setting up many features that maximize protection.
Introducing the all-new Improving Security Posture and Hardening PAN-OS Firewalls. Best Practice Assessment BPA Tool The BPA for next-generation firewalls and Panorama evaluates a devices configuration by measuring the adoption of capabilities validating whether the policies adhere to best practices and providing recommendations and instructions for how to remediate failed best practice checks. Much of the time its not obvious where the gaps are in the use of those features.
3192021 Attach a best practice Vulnerability Protection profile to the Security policy rules that allow access in to your management network to protect against buffer overflows illegal code execution and other attempts to exploit client- and server-side vulnerabilities. If a check returns a failing score the tool provides the justification for the failing score and how to fix the issue. To create a profile for the purpose of protecting your management interface clone the strict profile and then enable.
In short the Palo Alto Networks Best Practices Tool can give you a clearer picture of how your security appliance is utilizing the features that Palo Alto offers. The logic behind the best practice checks in the BPA was put together by a group of leaders from key areas across Palo Alto Networks including Product Management ETAC Professional Services Global Practice Support Customer Success and Business Development.
Day 1 Configuration What Does It Do Knowledge Base Palo Alto Networks
 Hackers Are Then Breaking Into Unprotected Hosts And Installing A New Crypto Mining Malware Strain Named Kinsing Https Www Zdne Malware Trend Micro Server
Hackers Are Then Breaking Into Unprotected Hosts And Installing A New Crypto Mining Malware Strain Named Kinsing Https Www Zdne Malware Trend Micro Server
Security Best Practices Checklist For Palo Alto Networks

 Best Practice Assessment Palo Alto Uk Partner London
Best Practice Assessment Palo Alto Uk Partner London
 Firewall Security Definition Firewall Security Security Cyber Security
Firewall Security Definition Firewall Security Security Cyber Security
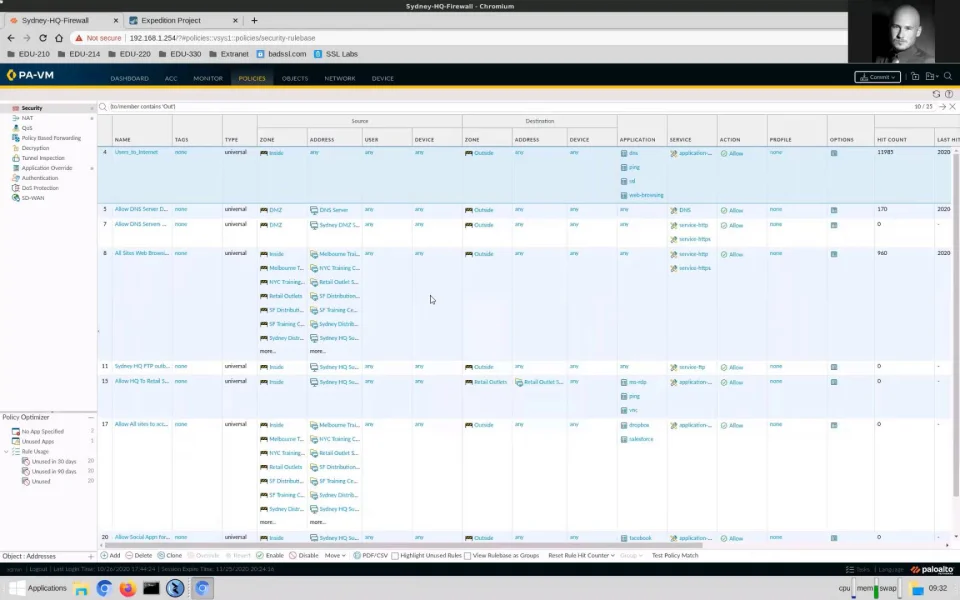 Firewall Hardening Best Practices For Palo Alto Networks
Firewall Hardening Best Practices For Palo Alto Networks
Security Best Practices Checklist For Palo Alto Networks
Optimize Your Security Policy Knowledge Base Palo Alto Networks
 Palo Alto Firewalls Configuration By Example Pcnse Prep 93 Off Udemy Coupon Code Palo Alto Online Courses With Certificates Udemy Coupon
Palo Alto Firewalls Configuration By Example Pcnse Prep 93 Off Udemy Coupon Code Palo Alto Online Courses With Certificates Udemy Coupon
 A Firewall Is A Network Security System That Monitors And Controls The Incoming Firewall Security Intrusion Prevention System Public Network
A Firewall Is A Network Security System That Monitors And Controls The Incoming Firewall Security Intrusion Prevention System Public Network
 Best Practice Training For Palo Alto Networks
Best Practice Training For Palo Alto Networks
 Full Best Practices Assessment Orange Cyberdefense Belgium
Full Best Practices Assessment Orange Cyberdefense Belgium
 Splunk Best Practices Python Javascript Angular Angularjs Reactjs Vuejs Webdev Perl Ruby C Csharp Java Linux Pro Best Practice Marlette Practice
Splunk Best Practices Python Javascript Angular Angularjs Reactjs Vuejs Webdev Perl Ruby C Csharp Java Linux Pro Best Practice Marlette Practice
 Firewall Software Market Is Projected To Exhibit A Cagr Of 7 From 2018 To 2027 Cisco Systems Fortinet J Cisco Systems Juniper Networks Palo Alto Networks
Firewall Software Market Is Projected To Exhibit A Cagr Of 7 From 2018 To 2027 Cisco Systems Fortinet J Cisco Systems Juniper Networks Palo Alto Networks




Posting Komentar untuk "Palo Alto Firewall Rules Best Practice"