Palo Alto Security Zones
When enabling log forwarding for a rule or rules the firewall will forward logs to the external server when the rule is a match. For example if you create a universal rule with source zones A and B and destination zones A and B the rule would apply to all traffic within zone A all traffic within zone B and all traffic from zone A to zone B and all traffic from zone B to zone A.
How To Configure Color Coded Tags Knowledge Base Palo Alto Networks
Palo Alto Networks Enterprise Firewall - PA 7000 Series Our PA-7000 Series high-performance network security appliances offer the perfect blend of power intelligence and simplicity.
Palo alto security zones. Although this basic security policy example configuration depicts using a single zone for all of your data center applications you should define more granular zones to prevent unauthorized access to sensitive applications or data and eliminate the possibility of. Palo Alto Networks firewalls allow administrators to forward logs to external servers. 10122016 Palo Alto Networks Next-Generation Firewalls have four main types of Zones namely as shown in the screenshot below.
212021 Security Zone Settings. These needs compel many organizations to seek ways to augment their security infrastructure. Use only letters numbers spaces hyphens periods and underscores.
4112018 I have a question on Palo Alto negate object. The Zones Palo Alto expertise stretches around the globe with offices and distribution centres around the world. Rule Based Log Forwarding.
Does it mean that the rule is allowing other src IP not including 101010024 from src zone A to dst zone B dest IP of ANY. You must have security admin permissions and access to your firewall virtual system vsys in order to adjust security policies and profiles. The same principles of zone selection apply for VPN tunnel interfaces when defining security policies.
To secure virtual networks security teams need to accomplish three main objectives. Palo Alto Networks DNS Security applies predictive analytics machine learning and automation to block attacks that use DNS. This video tutorial has been taken from Mastering Palo Alto Networks.
Power derived from a proven platform architecture that combines an ultra-efficient single-pass software engine with nearly 700 function-specific processors for networking security content. Traffic is processed by the security policy in a top-down left to right fashion. The name is case-sensitive and must be unique within the virtual router.
Security Zone Overview Security zones are a logical way to group physical and virtual interfaces on the firewall to control and log the traffic that traverses specific interfaces on your network. 4102019 Palo Alto Networks works in what they call security zones for where user and system traffic is coming and going to. This name appears in the list of zones when defining security policies and configuring interfaces.
Palo Alto Networks PA-5250 - security appliance. You can learn more and buy the full video course here httpsbitly2F37FZEFind us on. Enter a zone name up to 31 characters.
Zones and Palo Alto work with companies and organisations across the globe enabling digital transformation through next generation security and protection. Add to Shopping. 3192021 Zone Protection Profiles provide additional protection between specific network zones in order to protect the zones against attack.
Limit lateral threat movement respond quickly and effectively to intrusions and prevent information loss. An interface on the firewall must be assigned to a security zone. On the Palo Alto Networks firewall the security zone that is assigned to a specific interface is essential for establishing security policies based on traffic that needs to be allowed restricted or denied.
If I have a allow rule that allow src zone A src IP of 101010024 Negate to dst zone B dest IP of ANY. Log forwarding configuration can be found in security rules and also when defining a zone. The profile must be applied to the entire zone so it is important to carefully test the profiles in order to prevent issues that may arise with the normal traffic traversing the zones.
Tight integration with the Next-Generation Firewall gives you automated protections prevents attackers from bypassing security measures while comprehensive analytics allow deep insights into threats and empower security personnel. Palo Alto Firewall Security Zones can contain networks in different locations The above topology illustrated shows VLANs 10 11 12 and 2 managed by a Cisco Catalyst 4507RE Switch and are all part of OSPF Area 0 and visible as routes in the Palo Alto Firewall.
Configure Static Nat On Palo Alto From Lan To Dmz App Zone Uninets Blog
 Palo Alto Firewall Basic Configuration Zone Security Policy Nat Virtual Router Youtube
Palo Alto Firewall Basic Configuration Zone Security Policy Nat Virtual Router Youtube
 Network Security Memo Info Security Memo
Network Security Memo Info Security Memo
Zone Protection Profile Not Generating Logs During Penetration Knowledge Base Palo Alto Networks

How To Enforce Url Filtering Policy On Tls Handshakes For Decry Knowledge Base Palo Alto Networks
 Palo Alto Interfaces And Security Zones
Palo Alto Interfaces And Security Zones
How To Configure A Palo Alto Networks Device For Tap Mode Opera Knowledge Base Palo Alto Networks
 Mastering Palo Alto Networks Firewall Security Zones Packtpub Com Youtube
Mastering Palo Alto Networks Firewall Security Zones Packtpub Com Youtube
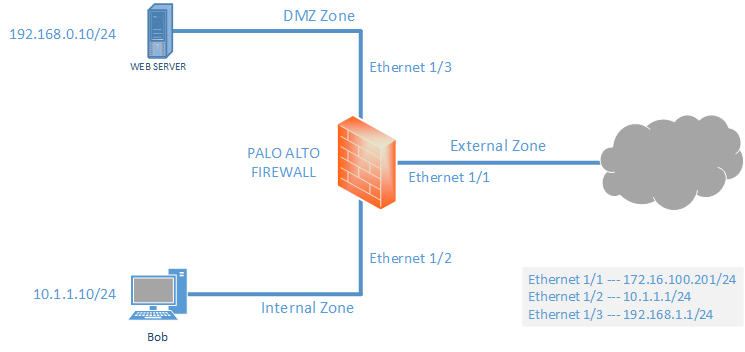 Palo Alto Zone Based Firewall Configuration Lab Letsconfig
Palo Alto Zone Based Firewall Configuration Lab Letsconfig
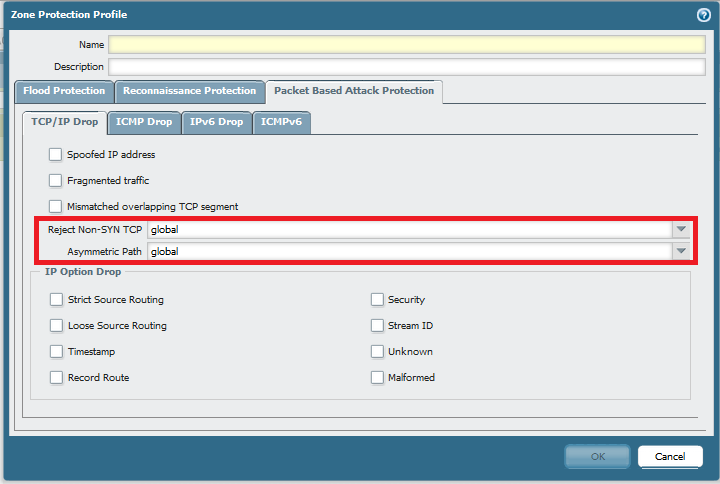 How To Set The Palo Alto Networks Firewall To Allow Non Syn Fir Knowledge Base Palo Alto Networks
How To Set The Palo Alto Networks Firewall To Allow Non Syn Fir Knowledge Base Palo Alto Networks
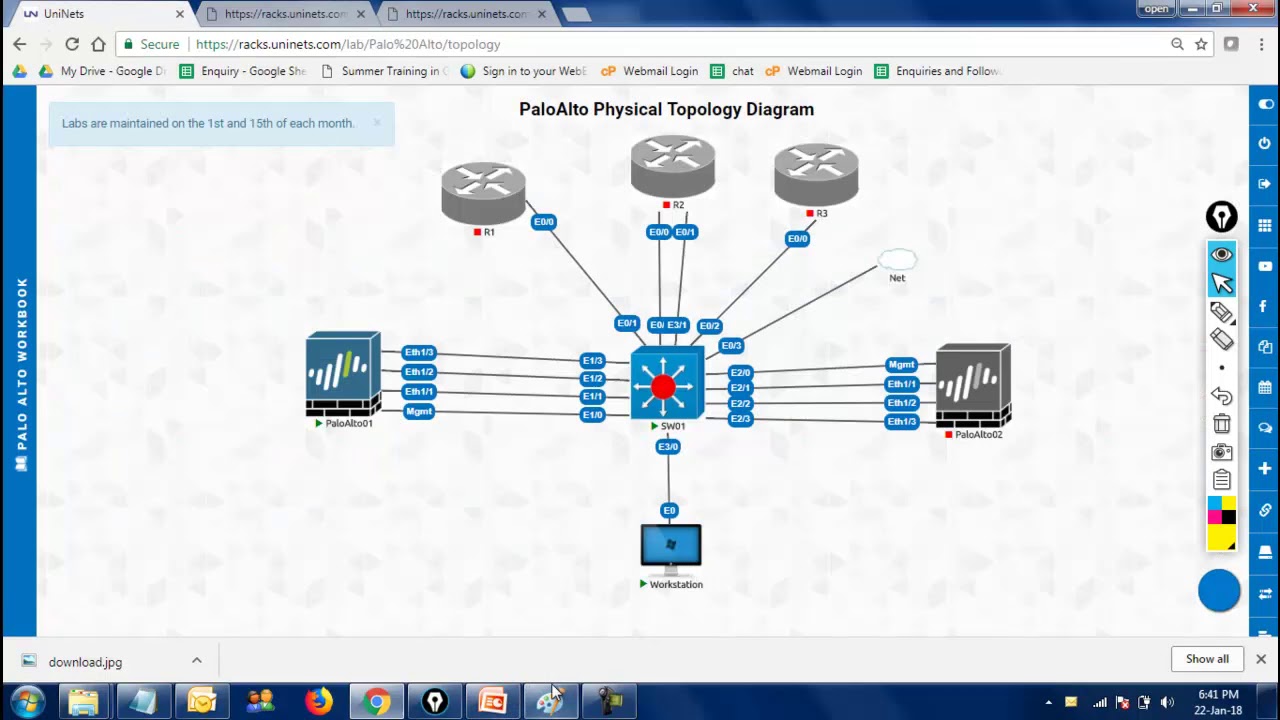 Palo Alto Firewall Training By Uninets Topics Security Zones Firewall Interface Virtual Wire Youtube
Palo Alto Firewall Training By Uninets Topics Security Zones Firewall Interface Virtual Wire Youtube
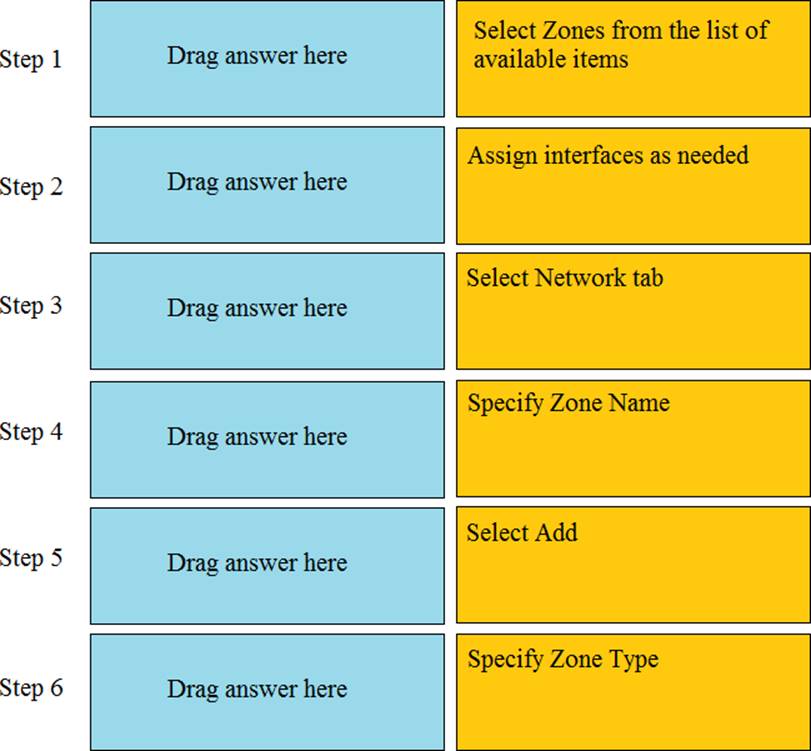 Order The Steps Needed To Create A New Security Zone With A Palo Alto Networks Firewall Exam4training
Order The Steps Needed To Create A New Security Zone With A Palo Alto Networks Firewall Exam4training
Security Policy Fundamentals Knowledge Base Palo Alto Networks
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks




Posting Komentar untuk "Palo Alto Security Zones"